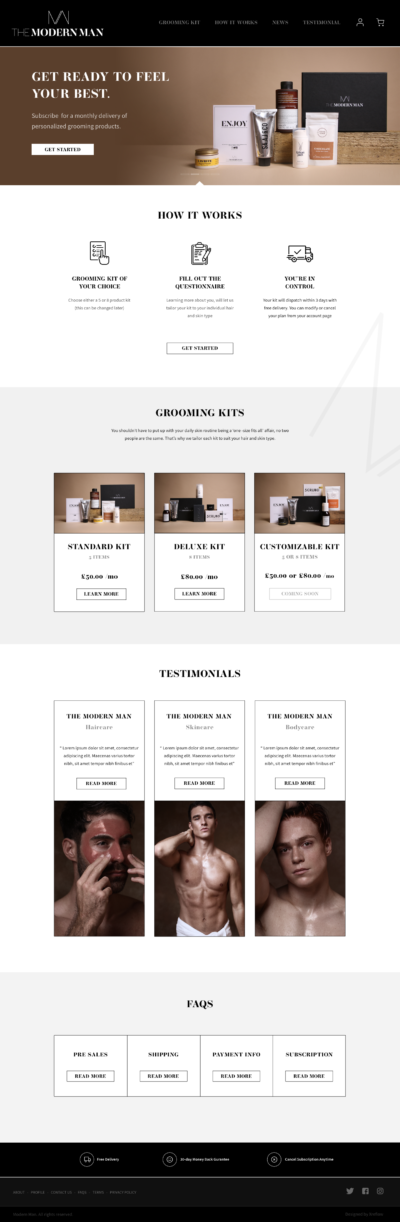
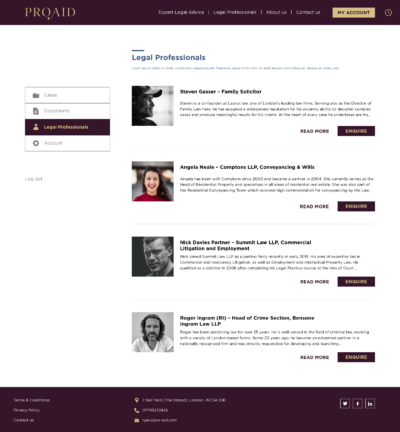
XRF is a collection of highly talented designers and developers with an amazing support team. We provide bespoke, high-quality mobile and web application development services to businesses throughout the world.
If you’re a brand new start-up or a multi-national corporate we’d love to hear your ideas. We pride ourselves in turning digital dreams into realities
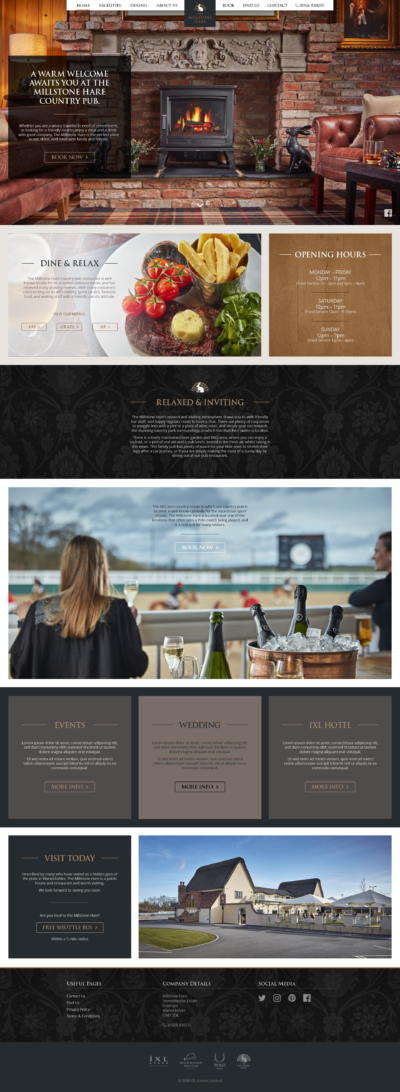
Case Study
Brief 2 Build
Brief2Build was a new business, they required a global hub to bring together both exhibitors and suppliers.
Two target audiences:
Suppliers-
To receive RFQ, Tenders and briefs of requirements from exhibitors.
Exhibitors-
To be able to upload requirements for conferences, shows trade events etc.. and to receive quotations in one easy action to save time and money.
The website needed to have e-commerce,
VIEW PROJECTWhat Our Clients Say
I thoroughly recommend Xreflow to provide a cost-effective website which is GDPR compliant done with minimal interruption."
J. Vine-Hall Sedlescombe Parish Council
I now have a fully functional website designed around all my needs and wants that will generate a lot of new business for me. The systems within the website have also bought me back time and now allows me to spend even more time on other aspects of growing my business.
Killian Murphy - Physique By Design
Also, the website is looking AMAZING and I am really happy with it...thank you all for your hard work.
Thomas Holroyd, Sign Connect
We turned to XReflow when another web developer was unable to support us. For the past year the team at XReflow have been an integral part of bringing our vision to reality. They are extremely knowledgeable and approachable and would thoroughly recommend their services.
Chris Eves - Skip For Hire
I approached Xreflow to design and host a website and email for my motorsport career. I used the in-house designers to create my site, it’s more than I even could of hoped for. All the team at Xreflow are really easy to deal with and always very professional and quick acting whilst going through the development stages. Would highly recommend them to anyone.
Paul Wood - Paul Wood Racing
As the Digital Designer at Teachers First, I chose XReflow to develop the website I designed. Dave, Managing Director, was extremely helpful and supportive from start to completion. He answered every question and request I had, and I have a website that perfectly matches my vision and design. Would highly recommend and would work with them again!
Teachers First
An extremely knowledgeable company, and always happy to help you out!
Debbie Callender
Thank you so much to the team for a fantastic service! First Page on Google! Cant beat that :) . I will be calling on your services again in the very near future.
Elite Life Coaching
Always on the end of the phone. Is like having your own IT department! Very impressed!
Annie Bee Portrait
Thanks for all your help. The site looks brilliant so please thank Ian and Charlotte for me.